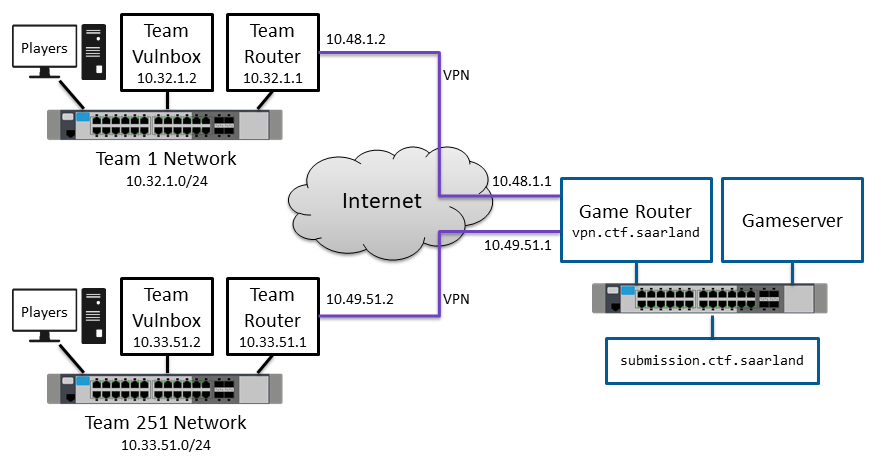
Summary
- Game network
10.32.0.0/15(10.32.0.0 - 10.33.255.255)- Team Network
-
10.(32+X).Y.0/24whereX := <team_id> // 200andY := <team_id> % 200 - Router IP
-
10.(32+X).Y.1 - Vulnbox IP
-
10.(32+X).Y.2 - Testbox IP
-
10.(32+X).Y.3
Cloud-hosted Setup
This year, we offer to host all required VMs for you in the cloud. When the game starts, you will be able to access your VM using SSH.
Players connect to the game network using OpenVPN - each player needs to install OpenVPN on his machine, no additional setup is required.
All players must have OpenVPN installed, we provide everything else.
- Download the cloud-hosted vpn configuration file from your team page (not the self-hosted one). Share it with all your players.
-
Every player uses this file together with OpenVPN to connect to the game VPN.
Check if they can ping
10.32.250.2from the Router. If so then the VPN connection works. - Store one or more public SSH keys on your team page. They will be deployed to your vulnbox later.
- When the game starts, go to your team page to create yourself a cloud-hosted VM. You then see its IP, you can use your private SSH keys to connect. It should be available a few minutes later.
- Do not use the regular (self-hosted) VPN configuration file together with the cloud-hosted vulnbox. It will not work (and likely break).
- You can change your SSH public keys at any time, changes will synchronize to your vulnbox within a few minutes.
Self-hosted Setup: Vulnbox, VPN and Network
As usual, you can host the vulnbox yourself. The Vulnbox will be delivered as encrypted VirtualBox image in OVA format. You need at least VirtualBox 5.2, newer is better. We suggest your host machine has at least 3 CPU cores and 4 GB RAM. We will provide a router image for your convenience and a test machine before the competition.
You need one machine to host the Vulnbox and act as VPN gateway (between your team network and our game network). Depending on your infrastructure there are different setups possible. We suggest our pre-configured Router VM image to save you most of the configuration.
- If you have a machine with two network interfaces (preferrably physical), we suggest setup 2 (Router VM + physical team network).
- If you do not have a machine with two network interfaces, use setup 3 (Router VM + team-internal VPN).
- If you know what you're doing, use setup 4 (manual setup).
- If you want to play online/remote without any hardware, use setup 5 (cloud based, not recommended)
You can see if your configuration works on vpn.ctf.saarland.
To test the other direction ping submission.ctf.saarland.
eth0
in this example) and connect your team-mates to your second interface using switches
(eth1), not routers. No configuration is necessary for your team-mates.
Follow these instructions to setup VPN and VMs.
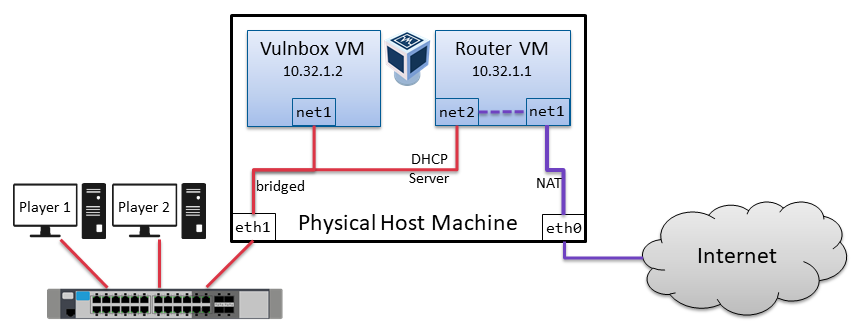
- Download and install Virtualbox, download all VM images.
- Import the Router VM and the Testbox VM to Virtualbox.
- Check the router's network adapter configuration:
- Adapter 1 should be NAT.
- Adapter 2 should be bridged to your secondary interface eth1.
- Once network adapters are properly configured, start the Router VM (not yet the Testbox).
- Connect to the Router VM:
- Either use the displayed console
- Or use SSH (exposed on port 22222 on your host):
ssh -p 22222 root@localhost. Password is123456789.
- Follow the setup assistant. Answer the DHCP question with yes. Answer the VPN question with yes if you have remote players.
- Copy your public SSH keys to
/var/www/html/saarctf/authorized_keys. These keys will be automatically deployed to the Testbox and Vulnbox later. - Copy the VPN configuration you received to
/etc/openvpn/saarctf.conf. Start the VPN withsystemctl start openvpn@saarctf. Enable permanently withsystemctl enable openvpn@saarctf. - Check if you can ping
10.32.250.2from the Router. If so then your VPN connection works. - Check the Testbox network adapter configuration: Adapter 1 should be bridged to your secondary interface eth1.
- Start the Testbox. If you added SSH keys to the router (step 7) and enabled DHCP (step 6) it should configure automatically. If not connect using display or serial console and follow the setup assistant.
- Login on the Testbox (use its network IP and your SSH key) and try to ping
10.32.250.2. If ping succeeds then your setup works.
- To setup the Vulnbox decrypt it (
7z x <file>.7z), then follow the instructions for the Testbox. - Internet access for the Vulnbox and Testbox is disabled by default.
To enable run
./internet-access-vm-enable.shon the router. - If you have remote players:
- Answer the VPN question with yes (while setting up the router VM). Your VM will expose port 1194 UDP on your host.
- Make this port accessible to your remote players.
- Copy
/root/team-vpn-client.conffrom the router, insert your public IP in the first line and distribute to your remote players. - Your remote players should setup OpenVPN to connect into the game network.
- If your host is headless check out vboxmanage or phpVirtualbox. This script might also be useful.
- If your experience connectivity problems after setting up the Router:
Sometimes it happens that the DHCP server on the Router VM pushes an invalid
default route to your host. You can see your routes using
ip route. If you see a default route via the Router VM just delete it:sudo ip route del default via 10.32.X.1
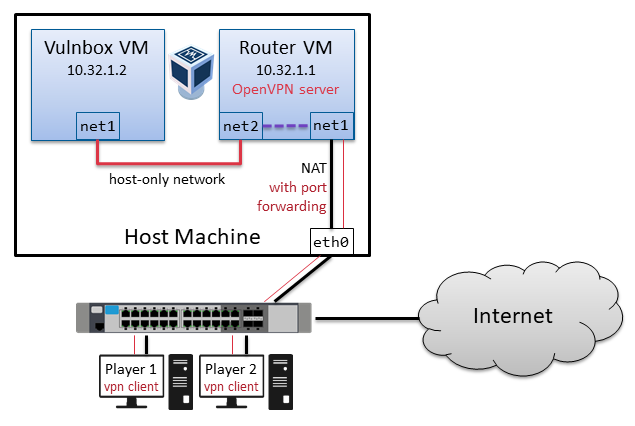
- Download and install Virtualbox, download all VM images.
- Import the Router VM and the Testbox VM to Virtualbox.
-
In Virtualbox create a new host-only network for your team network (stated above).
As of Virtualbox 6.1.28, you must explicitly allow the network range: add a line* 10.0.0.0/8 192.168.56.0/21to/etc/vbox/networks.conf. If that file does not exist, create it. - Check the router's network adapter configuration:
- Adapter 1 should be NAT.
- Adapter 2 should be switched to host-only and connected to your new network from step 3.
- Connect to the Router VM:
- Either use the displayed console
- Or use SSH (exposed on port 22222 on your host):
ssh -p 22222 root@localhost. Password is123456789.
- Follow the setup assistant. Answer both questions with yes.
- Copy your public SSH keys to
/var/www/html/saarctf/authorized_keys. These keys will be automatically deployed to the Testbox and Vulnbox later. - Copy the game VPN configuration you received to
/etc/openvpn/saarctf.conf. Start the VPN withsystemctl start openvpn@saarctf. Enable permanently withsystemctl enable openvpn@saarctf. - Check if you can ping
10.32.250.2from the Router. If so then your VPN connection works. - Check the Testbox network adapter configuration: Adapter 1 should be host-only in the same network as the Router.
- Start the Testbox. If you added SSH keys to the router (step 7) and enabled DHCP (step 6) it should configure automatically. If not connect using display or serial console and follow the setup assistant.
- Login on the Testbox (use its network IP and your SSH key) and try to ping
10.32.250.2. If ping succeeds then your setup works. - Copy
/root/team-vpn-client.conffrom the router, insert your host's local network IP in the first line and distribute to your team-mates. - Your team-mates should use OpenVPN to connect into the game network via your
host machine. If they can ping
10.32.250.2and the Testbox everything should be fine.
- To setup the Vulnbox decrypt it (
7z x <file>.7z), then follow the instructions for the Testbox. - Internet access for the Vulnbox and Testbox is disabled by default.
To enable run
./internet-access-vm-enable.shon the router. - If your host is headless check out vboxmanage or phpVirtualbox. This script might also be useful.
- If your experience connectivity problems after setting up the Router:
Sometimes it happens that the DHCP server on the Router VM pushes an invalid
default route to your host. You can see your routes using
ip route. If you see a default route via the Router VM just delete it:sudo ip route del default via 10.32.X.1
You're on your own. Use OpenVPN with the provided configuration to connect your machine to the game network. You can freely use your team network range, just ensure the Vulnbox gets the correct IP.
We know that it's sometimes hard to set up a Vulnbox on a system without monitor attached.
To easily setup the Vulnbox, you can use two shortcuts:
First use DHCP to assign the Vulnbox any IP from your team range (it will reconfigure to
10.X.Y.2 automatically).
Second have a webserver running on whatever machine is 10.X.Y.1 in your team range, which
serves a text file /saarctf/authorized_keys. If the Vulnbox can access this URL after
initial setup, it will enable SSH and install these keys.
Use the Testbox to test both steps.
You can play the game with two machines rented in the cloud. This is especially handy for teams that play together over internet. The following instructions assume you use Hetzner Cloud (where we also host our infrastructure), but in theory other cloud providers might also work out. Costs should be less than 1€ depending on your configuration. The following instructions assume that you already have an activated Hetzner Cloud Account.
-
Hosting the router
The router is the central machine for your team. It connects to Vulnbox and game VPN and hosts its own VPN server for your players.
-
Create a new "network" with IP range
10.32.0.0/11. Remove its default subnet and create a new one for your team network (for example10.32.99.0/24for team #99). - Create a new server "Router": select location Falkenstein, image "Debian 10", type "CX21", your network from step 1 and your SSH key.
- In Hetzner network settings, create a route for your network:
0.0.0.0/0, gateway is your router server. - SSH to the router server and install all software with our script:
wget 'https://ctf.saarland/static/scripts/install_cloud_router.sh' chmod +x install_cloud_router.sh ./install_cloud_router.sh - Fix routes to cloud machines (replace
32.99with your team network):ip route add 10.32.99.2/31 via 10.32.0.1 dev ens10 - Copy the game VPN configuration you received to
/etc/openvpn/saarctf.conf. Start the VPN withsystemctl start openvpn@saarctf. Enable permanently withsystemctl enable openvpn@saarctf. - Open
/root/team-vpn-client.conf, insert your server's public IP in the first line and distribute to your team. All players can use the same configuration file. - Check if the router and the players can ping
10.32.250.2.
-
Create a new "network" with IP range
-
Hosting the testbox
While the testbox is not strictly necessary, you can already try out the setup process you'll need for the vulnbox later.
- Create a new server "Testbox": select location Falkenstein, image "Debian 10", type "CX11" and your SSH key. No network!
- Attach the new server to your network in the network configurations, manually assign IP
10.X.Y.3. - Reboot the server into rescue mode ("enable rescue & power cycle, system "linux64")
- Download testbox archive and install script:
cd /dev/shm wget 'https://ctf.saarland/static/scripts/install_cloud_bundle.sh' wget 'https://vpn.ctf.saarland/vm/saarctf-testbox.tar.xz' chmod +x install_cloud_bundle.sh - Install the bundle:
./install_cloud_bundle.sh saarctf-testbox.tar.xz - Edit
/mnt/root/.ssh/authorized_keysand insert your SSH key again - Reboot
-
Hosting the vulnbox
Hosting the vulnbox is similar to the testbox, only IP, download URL and password differ. The password will be released when the game starts.
- Create a new server "Vulnbox": select location Falkenstein, image "Debian 10", type "CX21" or "CX41" and your SSH key. No network!
- Attach the new server to your network in the network configurations, manually assign IP
10.X.Y.2. - Reboot the server into rescue mode ("enable rescue & power cycle, system "linux64")
- Download vulnbox archive and install script once it is released:
cd /dev/shm wget 'https://ctf.saarland/static/scripts/install_cloud_bundle.sh' wget 'https://vpn.ctf.saarland/vm/saarctf-vulnbox.tar.xz.gpg' chmod +x install_cloud_bundle.sh - Install the bundle:
./install_cloud_bundle.sh saarctf-vulnbox.tar.xz.gpg <PASSWORD> - Edit
/mnt/root/.ssh/authorized_keysand insert your SSH key again - Reboot
Hints:
- Hetzner Cloud charges you for offline servers. After the game you must delete all machines.
- We advertise against using AWS: traffic is expensive there, we can't estimate your final costs
- To get better performance, you could run your exploits on the Router machine
- If team VPN performance is too bad, you can create multiple VPN servers on the router: Clone the configs and change the server port.
Service status
Every tick the Gameserver connects to your services and rates them in one of these categories:
- UP — Service is working, you receive SLA points
- Flag missing — Service is working, but flags from last tick could not be retrieved. No SLA points.
- Mumble — Service is accessible but non-functional.
- Offline — Service can't be accessed, error on network layer.
- Not checked — If your VPN connection is terminated, your service will not be checked.
If your service is broken, you can see more details in the scoreboard.
Flag submission
You can submit flags in a plain TCP connection to submission.ctf.saarland port 31337 from your
team network.
Each flag must be submitted in a single line terminated by a line feed (\n).
For each submitted line, the submission server answers with one line that starts either with
[OK] if the flag was accepted, [ERR] if the flag is permanently
invalid or [OFFLINE] if submission is currently disabled. This status is possibly
followed by a more detailed description.
A non-complete list of possible responses:
[OK][ERR] Invalid format[ERR] Invalid flag[ERR] Expired[ERR] Already submitted[ERR] Can't submit flag from NOP team[ERR] This is your own flag[OFFLINE] CTF not running
Status endpoints
The endpoint https://scoreboard.ctf.saarland/attack.json gives you a JSON with all
information you need during the competition. It is updated at the beginning of each tick. Format:
{
"teams": [
{
"id": 1,
"name": "NOP",
"ip": "10.32.1.2"
},
{
"id": 2,
"name": "saarsec",
"ip": "10.32.2.2"
}
],
"flag_ids": {
"service_1": {
"10.32.1.2": {
"15": ["username1", "username1.2"],
"16": ["username2", "username2.2"]
},
"10.32.2.2": {
"15": ["username3", "username3.2"],
"16": ["username4", "username4.2"]
}
}
}
}
"teams" contains a list of all teams that are online, including the IP of their
Vulnbox. If you limit your attacks to these IPs you can safe yourself some bandwidth.
Some services have "flag_ids", additional information that you might need for an
exploit. Usually this is the username of the Gameserver's account that you should attack.
The flag ids are only given for flags that are still valid.